Non-interactive authentication
Let's authenticate your users in Flex platform using the background channel
We recognize that for complex scenarios and for existing systems you would not want your users to create account in Flex to be able to use BIM functionality in your product. Therefore, for our partners we provide a higher privileged access to Flex platform where they can create Flex user identities as proxy objects for their users, they can log them in non-interactively using the background channel and they can manage access to all their resources in Flex from the API. This access is securely constrained to users and resources created by the partner. This allows our partners to use Flex platform as white-labelled service, fully integrated in their own products and services.
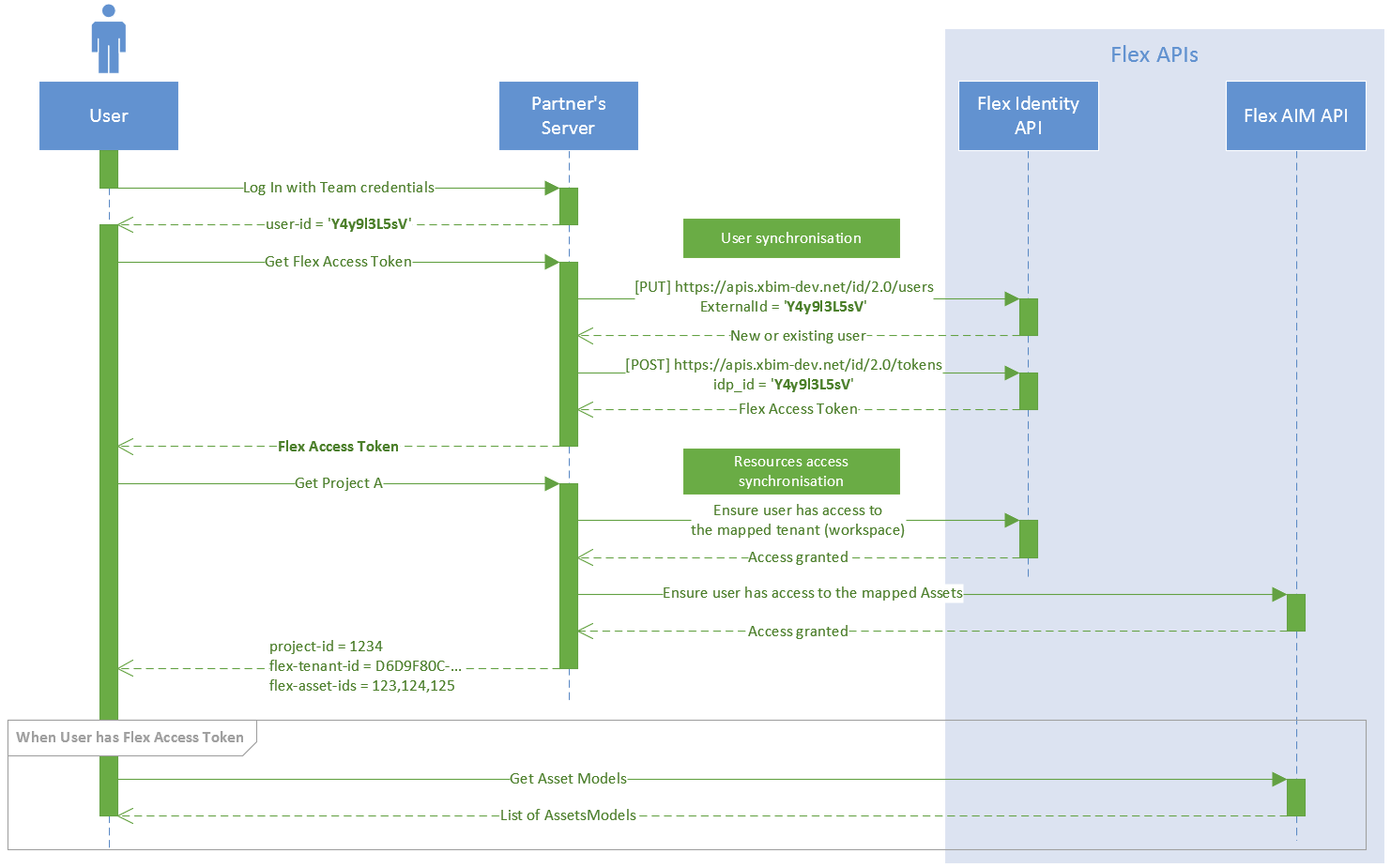
This sequence diagram shows this non-interactive workflow. As you can see, once the client retrieves the access token, end user application can use it to talk to Flex API directly. This is better for performance as we use a distributed reverse proxy, which optimises the traffic based on the geographical location of the original request and location of resources.
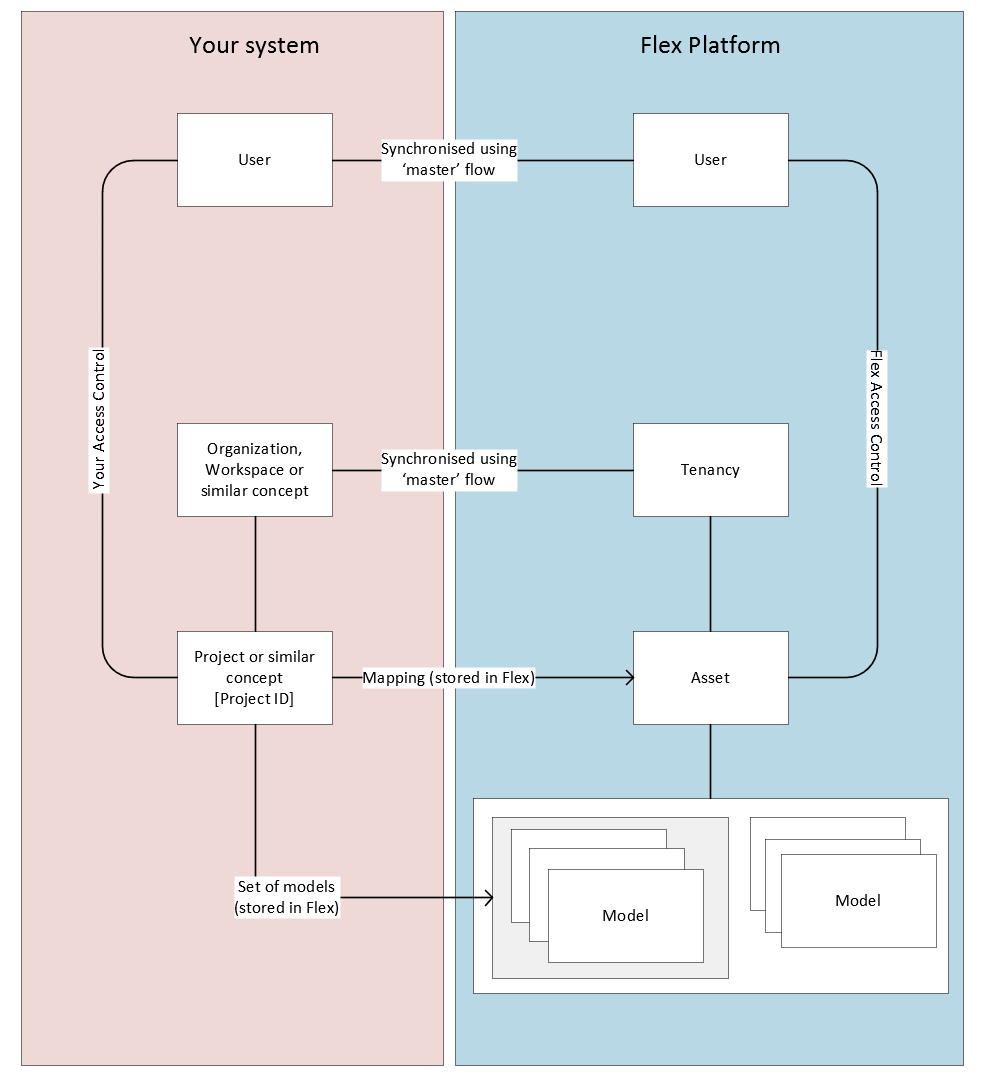
Given this level of access, our partners can easily map their business level concepts to Flex. Following diagram is an example of such a mapping, which leverages the power of fine-grained Flex access control:
To be able to use this functionality, we provide our partners with credentials allowing them to use the identity tokens endpoint. If you develop .NET web application, you can use our extensions component to integrate this authentication flow in your application. It will also help you to manage all your resources on the platform.
Updated about 2 months ago
